Exploring the Security Risks Posed by Data Brokers in the Context of t…
페이지 정보

본문
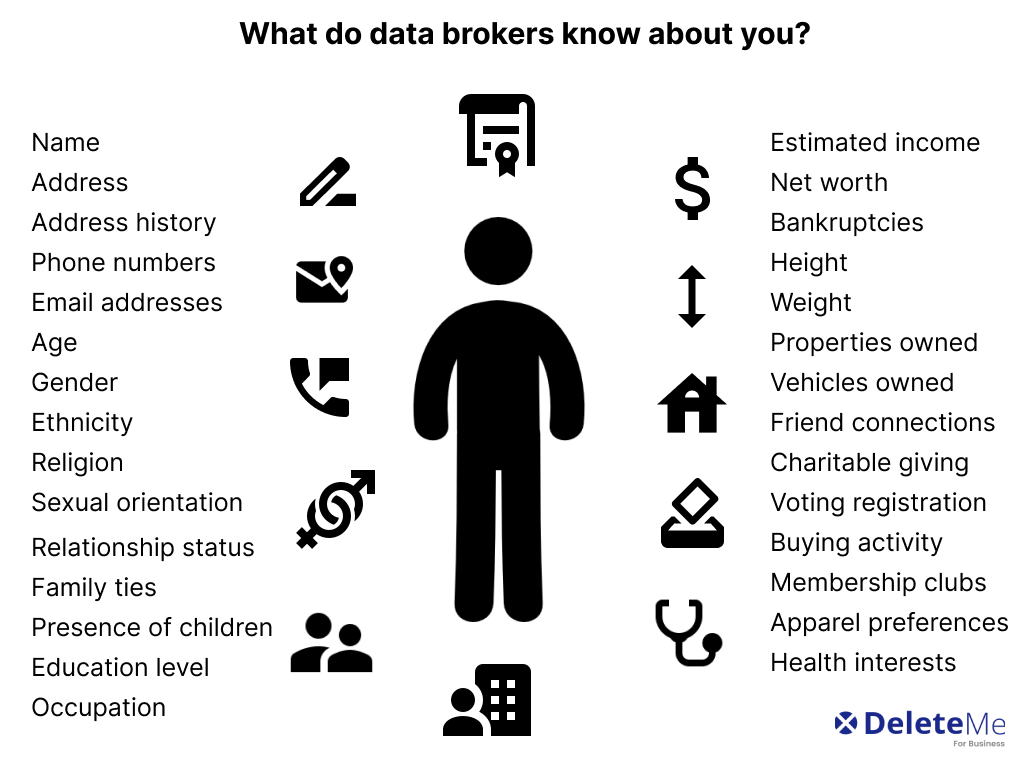
In our interconnected lives, numerous devices collect, share, and analyze personal information. This phenomenon has revolutionized both convenience and accessibility. However, lurking beneath this surface is a complex web of interactions that often goes unnoticed. Many consumers are unaware of how their information is utilized, and by whom. The implications of this exchange stretch far beyond mere convenience.
With countless devices constantly communicating, the potential for misuse is alarming. Vulnerabilities may arise, putting personal privacy in jeopardy. The invisible hands managing these exchanges often prioritize profit over protection. This poses significant challenges for individuals seeking to safeguard their private lives. As we navigate this landscape, understanding the chain of information flow becomes crucial.
Moreover, the myriad of platforms involved in processing personal insights adds layers of complexity. These systems, while designed for efficiency, can inadvertently expose sensitive details. As individuals become more reliant on smart technology, the stakes are raised dramatically. It is imperative to recognize that our choices may have unintended consequences, often beyond our immediate awareness. We find ourselves in a paradox where convenience meets potential danger, creating a precarious balance we must navigate carefully.
Understanding Data Brokers in IoT
In today's interconnected world, various devices constantly gather information from their environment. This collection process is rapid and often seamless. Smart gadgets, sensors, and appliances are designed to monitor and analyze user behavior. They send this information to external entities for further processing. This raises questions about who manages this data and how it is utilized.
Devices, ranging from simple wearables to complex home automation systems, collect user details continuously. They track habits, preferences, and even health-related metrics. This information is invaluable for many industries. It offers insights into consumer trends and helps enhance user experiences. However, the implications of collecting such extensive data are profound.
Organizations that specialize in aggregating and selling this information have emerged. These entities compile details from numerous sources. By doing so, they can create comprehensive profiles on users. These profiles can be sold to marketers, insurers, and others seeking targeted insights. Understanding this process is essential for consumers and policymakers alike.
Users often overlook the extent of information collected by their devices. The gathered data includes location, interactions, and usage patterns. This vast reservoir of information can be exploited if not adequately managed. While many benefit from personalized services, the underlying risks remain significant. The delicate balance between innovation and personal privacy presents ongoing challenges.
| Device Type | Information Collected | Common Uses |
|---|---|---|
| Wearables | Health metrics, activity levels | Fitness tracking, health insurance |
| Smart Home Devices | Usage patterns, preferences | Home automation, energy management |
| Connected Vehicles | Location, driving habits | Insurance calculations, traffic analysis |
Ultimately, as our reliance on connected devices grows, understanding how information is collected becomes crucial. Informed decisions can only be made when people comprehend the implications of this data exchange. Ongoing discussions regarding ethics, privacy, and regulations are essential to ensure a safer environment for users. Striking a balance between convenience and privacy will shape the future of technological advancement.
How IoT Devices Collect Data
Various devices interconnected within a network collect information from their environment, creating a vast pool of insights. These smart gadgets range from home appliances to wearable technology. They constantly gather, analyze, and transmit details that can significantly influence user experiences. Insight generation has become a hallmark of modern innovation. Everyday interactions lead to a continuous stream of valuable statistics.
Most modern devices incorporate sensors that track multiple metrics. These can include temperature, motion, sound, and even location. By employing these sensors, devices capture data that offer deeper insights into user behavior. Each interaction is a potential source of knowledge. For instance, a smart thermostat learns your preferences over time, optimizing itself based on your routines.
Moreover, connectivity plays a crucial role in the process. Devices often utilize Wi-Fi, Bluetooth, or other communication protocols to relay information. This seamless exchange is essential for real-time functionality. The ability to share updates promptly enhances the user experience. Information travels from one device to another, facilitating smarter environments.
Furthermore, cloud storage solutions enable devices to store and process large volumes of information. By offloading data management, these solutions allow for more complex analyses and the identification of patterns. This capability transforms raw inputs into actionable insights. The aggregation of information from multiple devices can lead to remarkably comprehensive profiles. As devices communicate, a network effect emerges, enhancing the overall value of the information collected.
Finally, it's essential to recognize the implications of such data collection practices. Users often exchange convenience for insights, sometimes without fully understanding the trade-offs involved. Awareness of how these processes operate is vital for informed decision-making. Ultimately, as technology continues to evolve, the methods and strategies for collecting valuable information will also adapt, constantly reshaping our relationship with smart devices.
The Role of Data Brokers
In today's digital landscape, the interaction between modern technology and individual privacy is becoming increasingly complex. Information collectors have established themselves as key players, influencing various aspects of our lives. They aggregate personal information, often without explicit consent from individuals. This situation raises important questions about autonomy and transparency. As a result, understanding how these entities operate is crucial.
Information collectors play a significant part in shaping user experiences. They gather insights from devices, analyzing behavior to create detailed profiles. These profiles are then sold or shared with various companies. This practice can enhance services but also poses critical challenges. While some customers benefit from personalized offers, many remain unaware of how their information is utilized.
Privacy concerns arise when considering how these practices affect relationships between users and corporations. When an individual interacts with smart appliances, wearable technology, or connected vehicles, their actions can be monitored. Each gesture, every command, can contribute to an extensive digital footprint. Consequently, individuals may unknowingly surrender control of their personal information.
Furthermore, the aggregation of insights from numerous sources has significant implications for trust. People often expect companies to respect their privacy, yet the reality is frequently different. These practices can lead to unintended consequences, such as loss of confidence in brands that misuse personal data. Therefore, awareness of these dynamics is essential.
| Impact of Information Collection | Potential Outcomes |
|---|---|
| Enhanced personalization of services | Increased consumer satisfaction |
| Loss of personal autonomy | Feelings of vulnerability among users |
| Manipulation of user behavior | Ethical concerns regarding consent |
| Trust erosion in brands | Long-term consequences for customer relationships |
Ultimately, the implications of information collection extend beyond individual experiences, affecting society as a whole. As technology continues to evolve, the importance of addressing ethical considerations cannot be overstated. Ensuring that individuals are informed about how their information is handled is paramount. Without this awareness, the potential for exploitation remains ever-present.
Privacy Risks in IoT Ecosystems
In today's interconnected world, personal devices continuously generate a vast amount of information. This influx can lead to significant challenges for individuals regarding their confidentiality. As smart gadgets become more prevalent, the potential for unauthorized access to sensitive details increases. It's crucial to understand the implications of this phenomenon.
When various gadgets communicate with each other, they create a rich tapestry of information exchange. This interconnectedness, although convenient, opens pathways for potential threats. Malicious actors may exploit weaknesses found in devices or networks. Consequently, individuals may unknowingly compromise their own privacy.
Consider how often we share personal preferences, health statistics, or even daily routines through our devices. Each interaction leaves a digital footprint, which can be collected and analyzed. These habits build a profile that, if misused, can severely impact one’s personal life. Moreover, the lack of robust safeguards often exacerbates the situation.
With numerous companies involved in capturing and selling this information, accountability becomes murky. Users often feel overwhelmed and unsure about who holds their data. The consequences of inadequate privacy measures can extend beyond mere inconvenience, potentially affecting one’s reputation or finances. Without clear regulations, maintaining control over personal information remains an uphill battle.
As more of our lives transition online, the importance of awareness grows. Individuals must educate themselves about potential threats associated with connected devices. By doing so, they can make informed choices about their gadget usage. Vigilance in this landscape can help mitigate adverse outcomes that may arise.
Ultimately, the entwined nature of smart devices and personal information necessitates a proactive approach. It is not just about enjoying the benefits but also about safeguarding what matters most. Individuals owe it to themselves to understand the environment they inhabit. Taking steps to opt out of spokeo to secure their information is essential for a safer digital experience.
Impact of Data Sharing on Security
In today's interconnected world, the sharing of information has become a double-edged sword. While it promises enhanced convenience and connectivity, it also brings forth a myriad of vulnerabilities. As devices communicate and exchange insights, the potential for threats looms large. Understanding the implications of this sharing is essential for both users and providers.
Every time information is transmitted, there is a chance it can be intercepted. Risks escalate when multiple entities are involved, each introducing its own set of weaknesses. Moreover, individuals often overlook the extent to which their personal details can be accessed. This lack of awareness can lead to severe consequences.
- Personal information can be misused for malicious activities.
- Unauthorized access to devices can compromise entire networks.
- Insecure transmission methods can expose sensitive data.
- Interconnected devices amplify potential points of failure.
In addition to these concerns, the aggregation of collected insights creates a profile that, when mismanaged, can be detrimental. When organizations rely on these shared resources without stringent controls, they inadvertently increase their vulnerability to breaches. An unsecured device not only threatens the owner but can also jeopardize the wider network it belongs to, raising alarm bells throughout the community.
The ramifications of compromised information can extend beyond immediate consequences. For instance, trust in technology may erode if users fear their information is not adequately protected. Such erosion could discourage individuals from adopting new technologies, stifling innovation and growth.
- Enhance encryption methods for all transmitted information.
- Implement strict access controls for sensitive devices.
- Regularly update software to address known vulnerabilities.
- Educate users on best practices for maintaining privacy.
Moving forward, organizations must take proactive measures to safeguard shared information. This includes fostering transparency about how insights are collected and utilized. Ultimately, building a culture of security around information-sharing will not only protect individuals but also lead to a more resilient technological landscape.
Mitigating IoT Security Threats

In today's rapidly evolving technological landscape, ensuring safety while using advanced gadgets has become paramount. Users often remain unaware of the vulnerabilities that accompany their devices. The integration of various systems increases exposure to potential dangers. Moreover, as these devices thrive on connectivity, risks multiply with every added element. Thus, combating threats requires a multifaceted approach that encompasses various strategies and practices.
First and foremost, manufacturers must prioritize security during the design phase. This means implementing robust encryption methods that safeguard communications between devices. Regular software updates play a critical role as well, addressing vulnerabilities that may arise post-launch. Additionally, encouraging strong, unique passwords enhances protection against unauthorized access.
Users also bear responsibility in this equation. Awareness is key. They should be informed about potential threats and how to mitigate them. Simple actions, like disabling unnecessary features, can significantly reduce exposure to potential attacks. Furthermore, utilizing network firewalls can act as an additional barrier against malicious incursions.
Moreover, collaboration among stakeholders is essential. Manufacturers, service providers, and regulatory entities must work together to establish comprehensive standards. Such cooperation could lead to the development of universal guidelines, improving overall safety for everyone involved. By sharing insights and experiences, these groups can better prepare for emerging threats.
Educating consumers about privacy implications associated with connected devices also holds great importance. Many individuals overlook how their personal information may be collected and utilized. Providing transparency regarding data collection procedures can foster trust and encourage informed decisions. Striking a balance between convenience and safety is crucial.
Ultimately, navigating this complex landscape requires vigilance. As technology advances, so do the methods employed by malicious actors. By staying informed and proactive, both manufacturers and users can significantly enhance the overall security framework. The journey towards a safer digital environment is ongoing, but with collaborative efforts, progress can be achieved.
Mitigating IoT Security Threats
Ensuring the safety of connected devices requires a multifaceted approach. As technology evolves, so do the vulnerabilities associated with it. This necessitates a proactive stance in safeguarding personal and organizational assets. Understanding potential dangers allows stakeholders to adopt effective strategies to counter them. Thus, the priority should be on establishing robust defenses.
Here are some key strategies to enhance protection:
- Regularly updating device firmware
- Changing default passwords
- Implementing strong encryption methods
- Conducting periodic security assessments
- Educating users about safe practices
Firmware updates often patch vulnerabilities that hackers could exploit. These updates might seem minor but play a critical role in maintaining device integrity. Furthermore, default passwords are frequently simple and easy to guess, making it essential to replace them with complex alternatives. Utilizing strong encryption ensures that even if data is intercepted, it remains unreadable. Continuous education for users about emerging threats can significantly reduce human error, which is often the weakest link in any security framework.
Another effective measure involves segmenting the network. By isolating devices from the main network, organizations can limit potential exposure. This technique creates safer zones where critical operations can continue without added risk. Additionally, utilizing firewalls and intrusion detection systems enhances monitoring capabilities. These tools can quickly identify suspicious activities and prevent unauthorized access.
Moreover, collaboration among manufacturers, regulators, and consumers is crucial. By working together, they can set industry standards that promote higher security levels. Transparency regarding vulnerabilities and breaches fosters trust. This cooperation ultimately leads to a more resilient ecosystem, where everyone is invested in improving safety.
Looking ahead, advancements in artificial intelligence offer promising solutions. AI can analyze patterns and detect anomalies that may indicate threats. Predictive analytics can foresee potential attacks and allow preemptive action. However, reliance solely on technology isn’t sufficient. A comprehensive approach, combining human vigilance with technological advancements, is vital.
In conclusion, mitigating threats related to connected devices requires ongoing effort and adaptation. By employing various strategies and fostering collaboration, individuals and organizations can create a safer digital environment. Embracing these practices not only protects assets but also enhances overall user confidence in adopting new technologies. The future hinges on our ability to tackle these challenges effectively.
The Future of Data Privacy
In an era where connectivity defines our existence, the landscape of privacy is evolving. Emerging technologies drive growth, but they also introduce complexities. Individuals increasingly face challenges in protecting their personal information. The balance between innovation and confidentiality becomes critical.
We’re witnessing a shift towards greater awareness. Consumers are more informed about their rights and options. This awareness fuels demand for enhanced safeguards. The future will likely involve stricter protocols.
Regulatory bodies are stepping up their efforts. New frameworks aim to provide clearer guidelines. Organizations will have no choice but to comply, ensuring transparency in handling sensitive information. As a result, businesses must adopt a proactive approach to risk management.
The role of technology cannot be overstated. Advanced tools such as encryption are becoming essential. These innovations empower individuals to regain control over their information. Additionally, artificial intelligence is being integrated into compliance mechanisms, enhancing monitoring and detection capabilities.
Collaboration between entities will play a pivotal role. Sharing best practices can lead to more robust defensive measures. Collectively, stakeholders must understand the importance of ethical practices. Mutual respect for privacy rights will foster trust and loyalty.
Moreover, education is vital. Consumers should be equipped with knowledge about their options. The more informed they are, the better decisions they make regarding their data. Future initiatives will likely emphasize this educational aspect.
Ultimately, the evolution of privacy is an ongoing journey. It will require commitment from all parties involved. As technology continues to advance, so too must our understanding of its implications. Therefore, a collaborative effort is necessary to shape a secure and respectful environment for everyone.
- 이전글Проведение отопления в доме: ключевые аспекты 24.10.21
- 다음글A Secrets And Techniques Buying Cheap Golf Clubs 24.10.21
댓글목록
등록된 댓글이 없습니다.
